-

2019 cyber security predictions
“With great power comes great responsibility.” Uncle Ben to Peter Parker (Spiderman) Happy new year! In the previous years we have seen a lot: ransomware, compromised elections, huge personal data hacks and more. Last year also saw regulations being enacted like GDPR. 2019 wont be any different. Bad guys will remain bad, and will remain […]
-

Non intrusive security audit
While ethical hack is an intrusive security scan, our non intrusive security audit compliments it by focusing on areas the ethical hack cannot. From getting your processor list in place to data classification, network to data flow diagram, fact finding questions to giving you our results in the form of a risk register, security audit […]
-

British Airways hack could provoke the wrath of the GDPR
More than 380,000 customer transactions on the British Airways website were compromised by hackers which included credit card information. If it’s determined that British Airways didn’t do enough to protect consumer information, it could be facing a fine of up to 4 percent of its annual revenue (that works out to about £500 million). Read […]
-

I know your secret and have recorded you doing something naughty…
Earlier this week, one of us received a very disturbing email. It basically said that using a malware they have recorded the individual via webcam watching an adult site. As evidence and to sound more convincing an old password of was revealed. This obviously was a sextortion scandal and we however were at ease as […]
-

It’s our Anniversary. Cheers to security.
Although the idea of having a proper security division was lingering for long, we finally took the plunge a year back. The plan involved recognising a separate division, building a team, working on a methodology, framework for security review/audit and penetration test, documentation, keeping an audit trail, and even making a new website. On 20/06/2017 […]
-
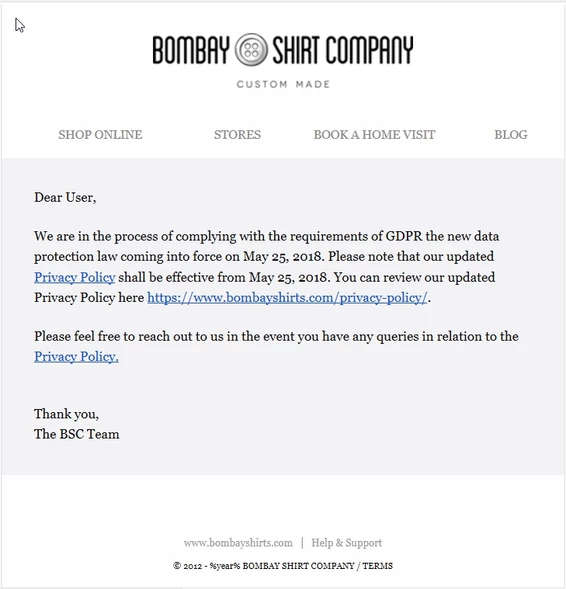
Indian shirt company’s proactive GDPR compliance
GDPR is affecting everyone in some form or the other, which was obvious when I received this email on the GDPR compliance process from an online shirt company in India on the 24th of May 2018 (just a day before the law comes in force). They announced they are in the process of GDPR compliance […]
-
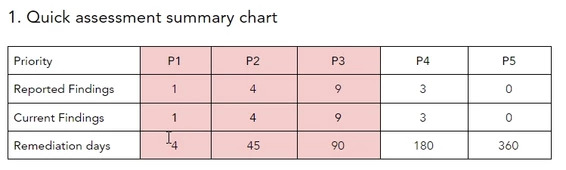
Code injection found in our latest web vulnerability assessment
Our latest web vulnerability assessment was unique not only because we had the highest findings till date (30 issues) but more because we found a code injection. While MySQL injections allow you to inject SQL commands on your database and may cause sensitive data from the database to be leaked, the code injection allows you […]
-

25 vulnerabilities found in our latest penetration test
Our latest penetration test was a quite tricky one! The application is huge and it took us much longer to finish the assessment than expected. Even though we had not budgeted for this we stayed committed and managed to pick up quite a few vulnerabilities. This was also the first time we included methods that […]