Recently we had an opportunity to conduct a security audit of a company that is involved in providing statistical insights to a wide number of clients.
Unlike a penetration test this is a non intrusive approach to audit their processes instead of an application. It requires understanding of the processes, how the company works, how data is collected, how it gets processed, what are the intermediate steps involved in the processing, and how the final output is generated.
The general impression usually is that since someone does not explicitly process any PII data (Personally Identifiable Information) there is no reason to worry much about security. But that is not true at times. So for this case our security analyst went deeper into the processes and
- we realized that there are cases where clients may send some exported raw data for processing which might accidentally contain PII data. Our experts then pointed out the need to have a preprocessing operation for PII cleanup of the data. Our team also created necessary templates for systematically tracking this process.
- at times, the data even though it may not contain any PII fields, may have business-sensitive data or data which may have financial implications if leaked. A simple example could be the export of sale of items. Even though it may only contain item details and the quantity of sale, from a business point of view it can give a lot of information to competitors if leaked. It can show which items sell quicker, when is the demand high for such items, etc.
The whole exercise of this security audit took about 6 weeks. The steps we took were
- Our security auditor began a one-to-one interaction with the client-side and noted down all the relevant information.
- Post that there was an internal discussion with the team to compile and process this collected information.
- With this processed information as the starting point, we tried answering various questions along with inputs from clients.
- To help understand the process we helped the client create a supplier/processor list and DFD (Data Flow Diagram). DFD helps in understanding the business processes and flow of data quickly and easily. You can read more about the supplier/processor list in our previous blog post: https://www.sapnasecurity.com/single-post/supplier-processor-list.
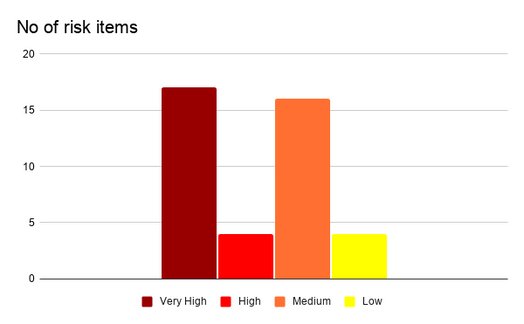
- After we had completed answering the questions we prepared a risk register and assigned risk values to all the items.
- The team is currently in touch with the client to explain and mitigate the risks, i.e we helped create key organizational policies related to clear desk, internet usage, email usage, password policy, etc.