-

10 Security Mistakes Developers Still Make in 2026
Despite major advances in security tools, automated scanners, and secure frameworks, many real-world breaches still happen because of simple development mistakes. These issues are rarely caused by sophisticated attacks; instead they arise from small oversights in application logic, configuration, or coding practices.Below are ten security mistakes developers continue to make in 2026 — and how…
-

Understanding OWASP A10:2025 – Mishandling of Exceptional Conditions
In the latest OWASP Top 10 update, a new category has been introduced: Mishandling of Exceptional Conditions. This entry focuses on something many teams overlook – what the application does when things go wrong. Security discussions usually center on well-known issues like SQL injection or broken access control. But modern systems are complex, distributed, and…
-

Important Infrastructure Update: Upgrading to Debian 13 for Enhanced Security & Performance
At sapnagroup, maintaining the security and performance of your digital assets is our top priority. As part of our commitment to proactive maintenance, we are upgrading our server infrastructure from Debian 11 to the latest Debian 13 operating system. Here is what you need to know about this transition. Why the upgrade is necessary?Some of…
-
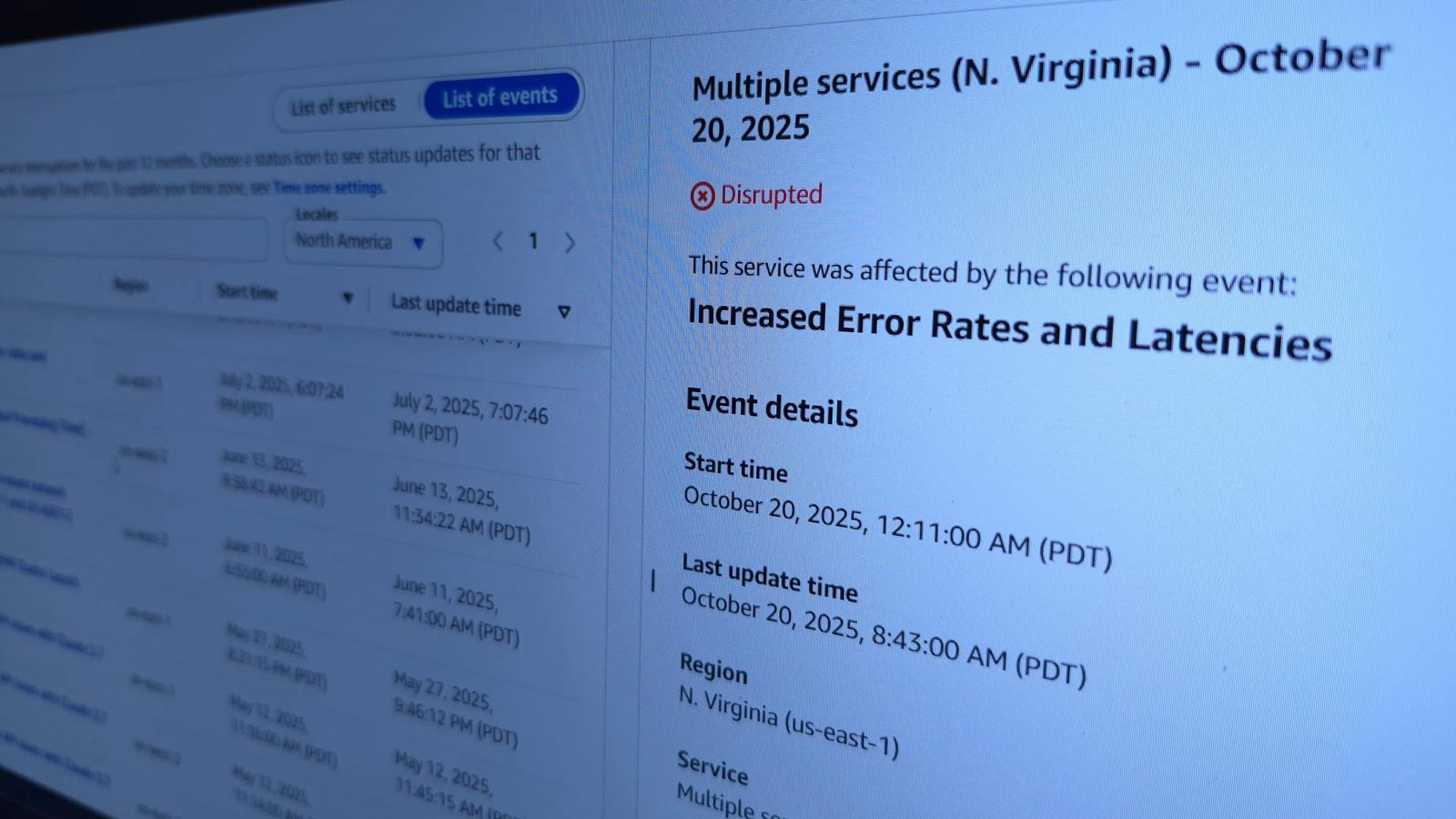
Lessons from the AWS Virginia outage: why business continuity planning is non-negotiable
The incident!On 20 October 2025, at 07:11 AM GMT, Amazon Web Services (AWS) experienced a major disruption in its US-East (Virginia) region — one of its oldest and largest data centres. The incident triggered a chain reaction across the internet, temporarily taking down or slowing thousands of websites, mobile applications, and cloud-hosted services around the…
-
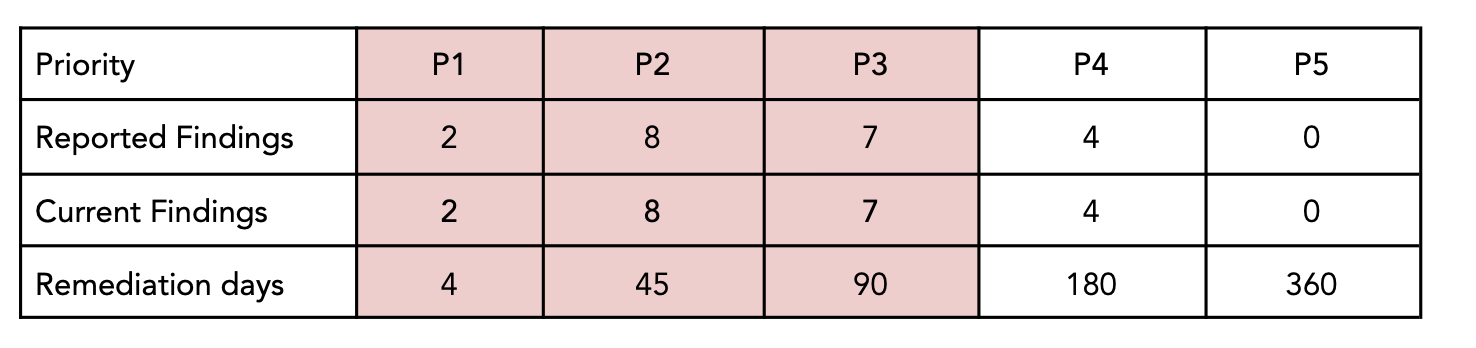
Cracking the Code: How Our Pentest Uncovered Critical Vulnerabilities in a web application
Strengthening Web Application Security: A 9-Day Pentest Success StoryAt sapna security, we recently got a go ahead with a web application to conduct a comprehensive penetration test (pentest) aimed at uncovering security weaknesses. The client provided us with a dedicated test environment, and over the course of 9 days, our security team performed a deep-dive…
-

FAQ for European Accessibility Act (EAA) enforced on 28th June 2025 and WCAG 2.1 Level AA
Note this is a general document for reference and we ask you to refer to your legal department for the correct scope and coverage of the law.
-

How Secure Is Your Website? 10 Critical Questions Every Site Owner Must Answer
Why you need to ask yourself these questions? In today’s digital landscape, your website is more than just a business card, it’s often your most public-facing and vulnerable asset. Whether you’re running an e-commerce store, a corporate site, or a personal blog, attackers are constantly scanning the web for weak points to exploit. From stolen…
-

Skype is Shutting Down – Transitioning to Google Chat & Meet
As you may have heard, Microsoft is officially shutting down Skype on 5th May 2025. To ensure a smooth transition, we are moving to Google Workspace Chat and Google Meet as our official communication platforms for chat and video calls. For those clients and partners who require Microsoft Teams, we will continue to offer support…
-

How to Protect Your Business from Email Scams
Real-World Email Scam Incident A few days ago, one of our clients received an email from Jonny, appearing as a continuation of an existing thread of correspondence. However, it was actually a scammer impersonating Jonny, attempting to change our bank details to divert a deposit to their own account. How the Scam Worked The scammer…