-
Code injection found in our latest web vulnerability assessment
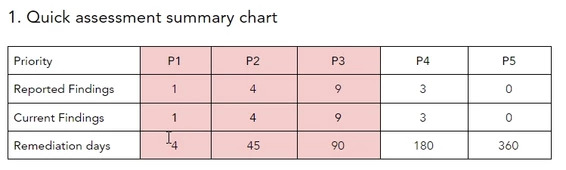
Our latest web vulnerability assessment was unique not only because we had the highest findings till date (30 issues) but more because we found a code injection. While MySQL injections allow you to inject SQL commands on your database and may cause sensitive data from the database to be leaked, the code injection allows you […]
-
25 vulnerabilities found in our latest penetration test

Our latest penetration test was a quite tricky one! The application is huge and it took us much longer to finish the assessment than expected. Even though we had not budgeted for this we stayed committed and managed to pick up quite a few vulnerabilities. This was also the first time we included methods that […]
-
Old browsers will stop working on some https sites (Hardening Webserver SSL/TLS Protocols and Cipher)
Whenever you connect to an https (encrypted) site, your browser and the site agree on one of the many encryption protocols available between them. Some of these protocols are old, and are now considered less secure and hence vulnerable. The only reason they were kept around is because of compatibility with old browsers, since the […]
-
Risk management and risk register for your organisation
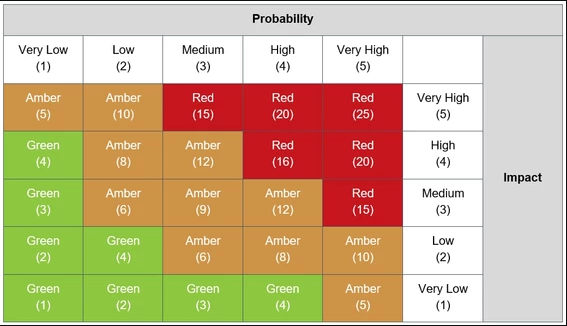
Risk management while sounding threatening and complicated is really very simple; you need to identify/list all the risks, prioritise them, and then find effective and economical ways to reduce these risks. This is also an important GDPR requirement. The steps needed to follow are Identifying risks: find out what could cause harm. A good group […]
-
Scope of the web application assessment (penetration test)
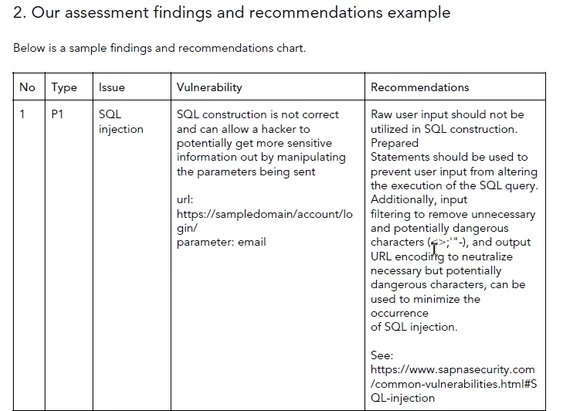
sapna security has a team which has years of experience on web architecture and applications and their vulnerabilities. Accordingly we have created a strong web application assessment list which includes the following areas: Injection Authentication Session Management Cross Site Scripting (XSS) Insecure Direct Object References Sensitive Data Exposure Access control Cross-Site Request Forgery (CSRF) Unvalidated […]
-
March, September 2018 deadline for some SSL/TLS certificates
Whats the fuss about? Google accused Symantec Corporation of series of failure to properly validate certificates. Google accordingly proposed that they will effectively withdraw Chrome browsers trust in all certificates issued by Symantec. Any resolution? Digicert acquired Symantec and a compromise was reached by Google to accept the certificates till some time. Symantec certificates will […]
-
Ethical hacking for UNICEF

We recently conducted a penetration (ethical hacking) for a site of UNICEF. Our expert team members managed to find vulnerabilities as can be seen in the snapshot below. We have also finished the remediation process by helping close and/or lower these findings after fixes were done.
-
Password guideline for general users
News portals are filled with reports on compromised accounts. We know friends who have had their Facebook, Yahoo, and other accounts hacked and can no longer access making them exposed to their sensitive emails, and even allowing hackers to pose as someone else. While application developers do their best to ensure safety, the first basic […]
-
Our internal staff training approach
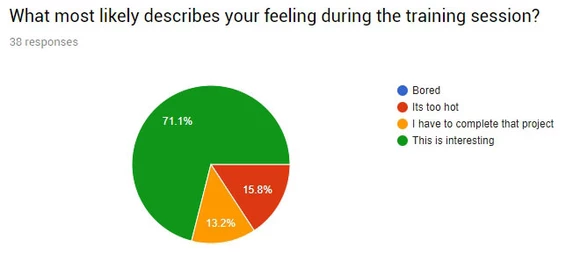
Internal staff training is an important step for any organisation for improving efficiency, skillset and policy/security awareness. The ICO even has a checklist for small and medium sized organizations https://ico.org.uk/media/for-organisations/documents/1606/training-checklist.pdf In Sept 2017 we started a new approach to our staff training session and system. The approach we followed was Created a training group which […]