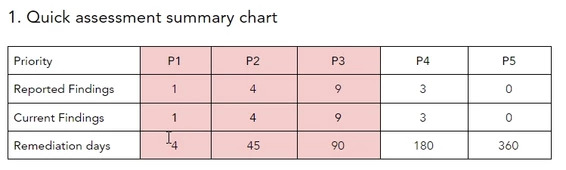
In the latest ethical hack conducted by our security team on a security related service, we managed to find a very interesting OS command injection finding which is Priority level 1.In the latest ethical hack conducted by our security team on a security related service, we managed to find a very interesting OS command injection finding which is Priority level 1.
OS command injection allows you to execute a system command on the OS. Our team used Burp to find this issue.
Our security team worked with the server and development team to isolate this specific finding and help fix it within a day.
However good you may consider your application/service and team that built it, without performing an ethical hack and security audit you can never be sure if there are vulnerabilities. We always advise to conduct annual ethical hack and security audit, as well as every time you have done major development changes.
Please see extract from our official report below
--snip-->
The filename multipart parameter attribute appears to be vulnerable to OS command injection attacks. It is possible to use the pipe character (|) to inject arbitrary OS commands. The command output does not appear to be returned in the application's responses, however it is possible to inject time delay commands to verify the existence of the vulnerability.
The payload |ping -c 21 127.0.0.1||x was submitted in the filename multipart parameter attribute (refer figure 386-a). The application took 20492 milliseconds to respond to the request, compared with 0 milliseconds for the original request, indicating that the injected command caused a time delay.
Also, The payload nslookup shell command |nslookup -q=cname <hidden data>& was submitted in the filename multipart parameter attribute (refer figure 386-b). The Collaborator server received a DNS lookup of type CNAME for the domain name <hidden data>. The lookup was received from IP address <hidden data> at <hidden data> UTC.
Affected URL: <hidden data>
parameter: filename
<--snip-